March 2019 Security Update Advisory (CVE-2019-9197)
Vulnerability Details
CVE ID: CVE-2019-9197
Type: Remote Code Execution
Discovered: 2018/11/15
Discovered By: rgod of 9sg Security Team - rgod@9sgsec.com working with Trend Micro’s Zero Day Initiative
Patch Availability: 2019/03/04
Affected Operating System: Windows
Affected Versions: All (Windows)
Severity: High
Patch Versions:
- [1] 2019.2.0a7 (Win), size= 795,664bytes, md5=6fcde1045cc4af7f84ba4f820f5db868
- [2] 2019.1.0b5 (Win), size= 696,212 kB, md5: d2ec9e0dc974adfd0e465ffe2e3f1c23
- [3] 2018.3.7f1 (Win), size=570,279kB, md5=6fcde1045cc4af7f84ba4f820f5db868
- [4] 2018.2.21f1 (Win), size=580,009kB, md5=1b87b98c936c81148a99c879386e676c
- [5] 2017.4.22f1 (Win), size=527,486kB, md5=8cb0783f22dc5bfc80d2f170472aefbf
- [6] 5.6.7f1 (Win), size=554,855kB, md5=d761d8c151007ce2474ddc9d468abc02
An input string validation issue was identified in the Unity Editor affecting the Windows platform that could lead to Remote Code Execution (RCE), allowing an attacker to potentially execute code remotely in the user’s computer.
Remediation Steps
Determine the version of your Unity Editor
Open a Unity project.
The Unity version is visible in the main window title.
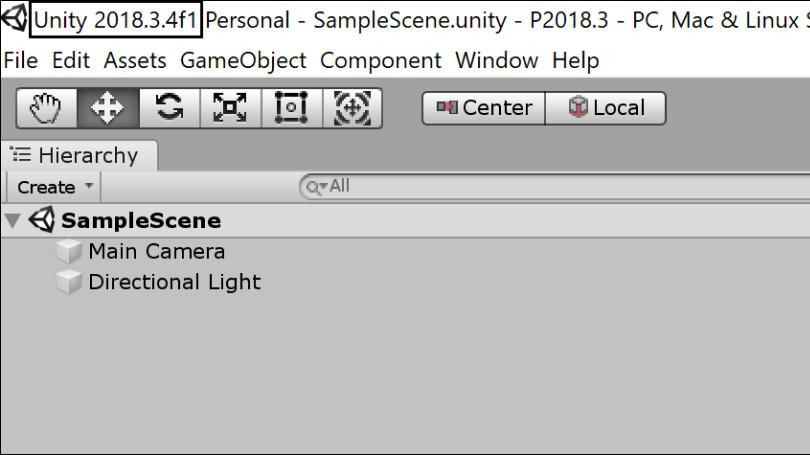
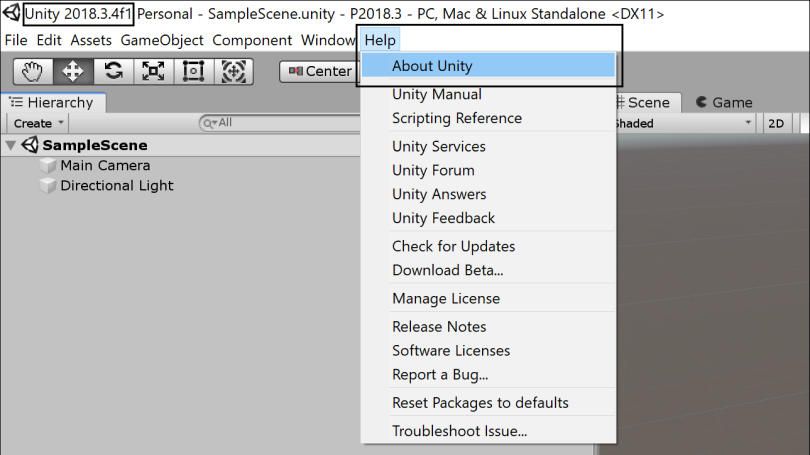
In the File menu choose Help -> About Unity.
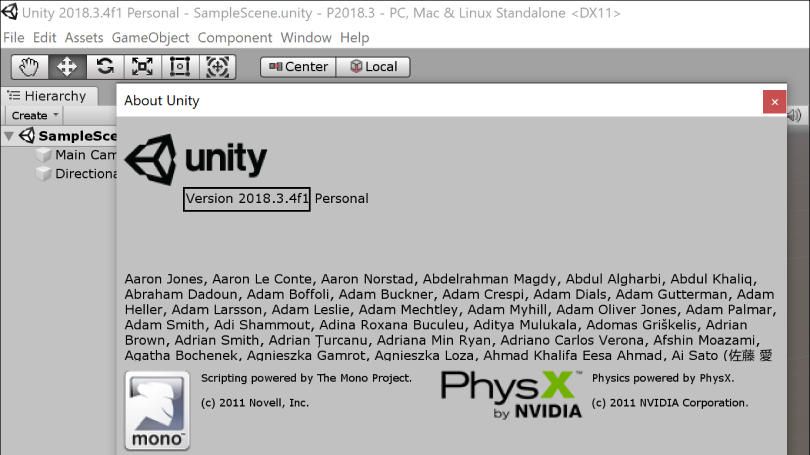
The Unity version is shown in the About Unity window.
Install Update
If your version of the Unity Editor is not one of the listed in the Patch Versions of the Vulnerabilities Details section above you can continue with the update installation as follows.
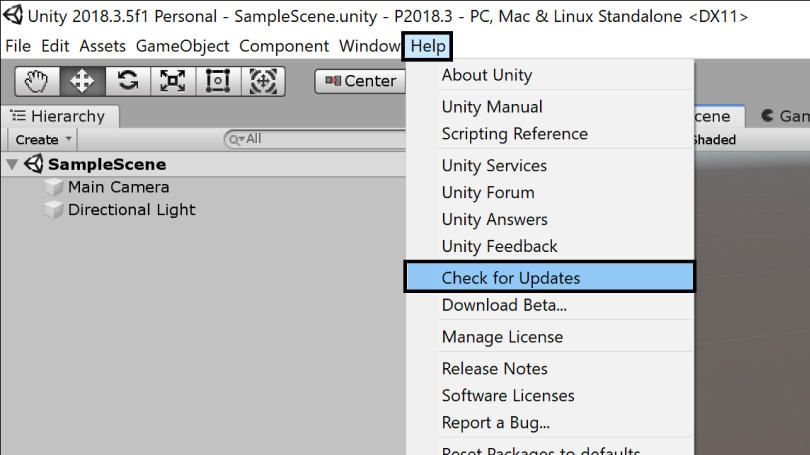
To install the update you can use the Unity Editor update checker available in the File menu Help -> Check for Updates.
Additionally, you can download and install the corresponding patch for your version of the Unity Editor. The download links are available in the Patch Versions of the Vulnerabilities Details section and in the References section.
Mitigation Tool
If your version of the Unity Editor is not listed, or you are unable to install the update at this time, you can use the Mitigation Tool Guide [7].
Please keep in mind the recommended action is to install a fixed version of the Unity Editor.
FAQ
What type of vulnerability was addressed in this update?
+Does this vulnerability affect built games/applications in any way?
+What platforms are affected?
+What versions of Windows are affected?
+What versions of Unity are affected?
+What versions of the Unity Editor are being patched?
+Will my specific version be patched?
+What about versions older than 5.6?
+Does the mitigation tool work for versions newer than 5.6? Can I use the mitigation tool instead of patching?
+I run multiple versions of Unity, do I have to apply the mitigation tool for all of them?
+Can I just use the mitigation tool and never move to a patched version?
+I have a locked-down older version of Unity 5.x.x. Will you produce a patch for the exact version of Unity that I’m using?
+Will I need to rebuild asset bundles due to the update requirement?
+How do I know if I’ll need to rebuild my asset bundles?
+References
- [1] 2019.2.0a7 (Win)
- [2] 2019.1.0b5 (Win)
- [3] 2018.3.7f1 (Win)
- [4] 2018.2.21f1 (Win)
- [5] 2017.4.22f1 (Win)
- [6] 5.6.7f1 (Win)
- [7] Mitigation Tool Guide
- [8] Mitigation Tool